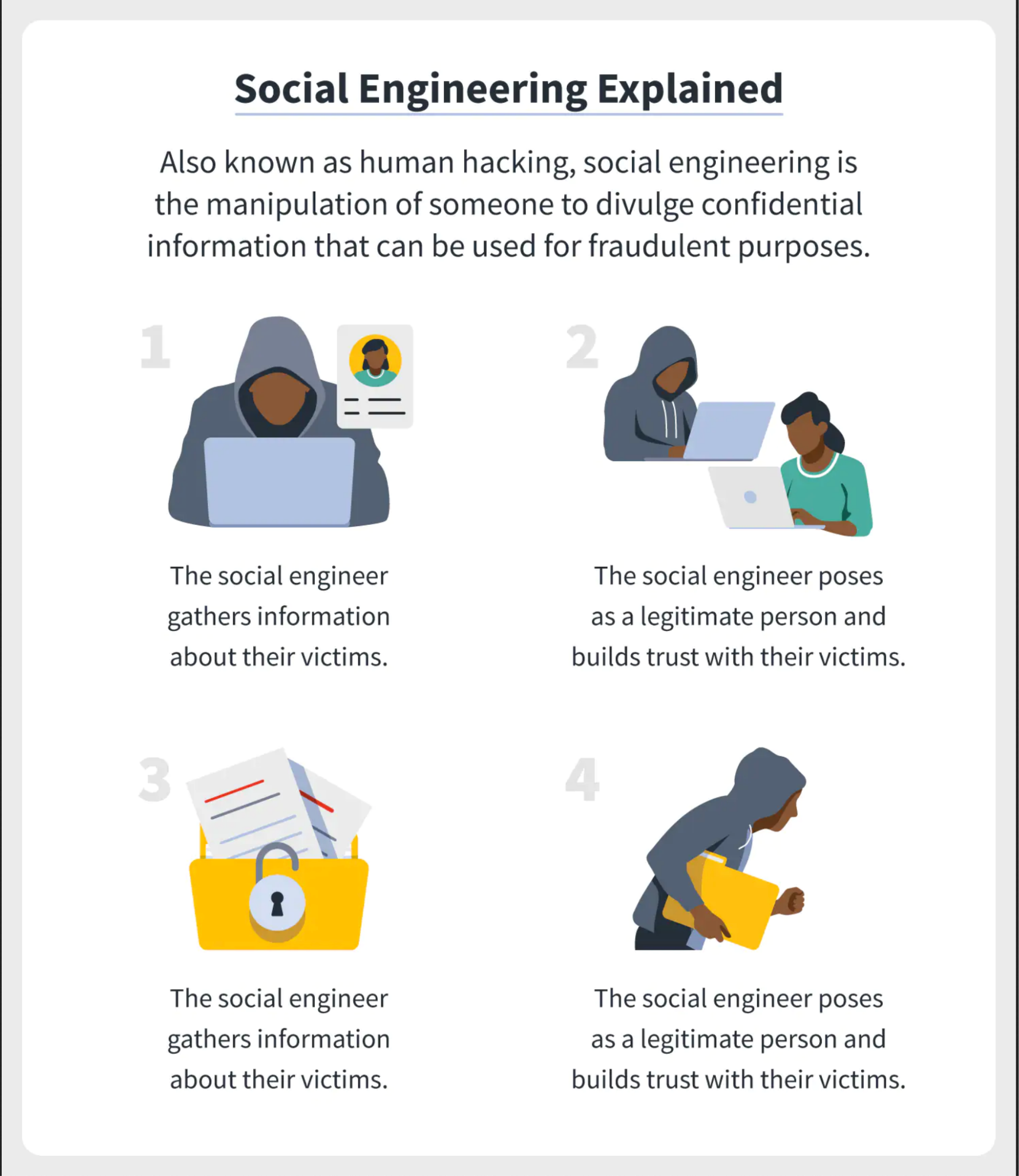
What is Social Engineering?
According to a study by Proofpoint in 2019, 98% of cyberattacks use social engineering tactics to achieve their goals. 98%. Understanding social engineering and the tools attackers use to gain your trust is key to effectively mitigating the risk of a cyberattack on you or your business.
Fortinet defines social engineering as “a wide range of attacks that leverage human interaction and emotions to manipulate the target.” The victim is tricked into providing compromising information which usually involves several steps.
- The cyberattacker will study the behavior of the intended target. They use this research to execute the attack by learning the likes or dislikes, businesses they engage with or don’t, etc, and their role in bypassing security protocols.
- As humans, we naturally are attracted to those we trust, whether it be a friend, spouse, or business. Social engineers know this and will try to facilitate a feeling of trust and common interests. They will use the information gained in their research to acquire the target’s trust.
- Once they have gained your trust, they begin manipulating the target to get sensitive information or violate security policies.
5 Human Characteristics Social Engineers Exploit
All humans have similar characteristics that social engineers know of and use to exploit their target. According to Fortinet, they are:
Liking – we tend to trust those we like. An email from a trusted vendor or customer, or even coworkers or bosses, is more likely to be opened and the requests fulfilled than one from an unknown source.
Spoofing an email identity is simple. All an attacker would need to search your websites or social media profiles, and they can easily create a false identity from someone you trust.
Reciprocity – Who isn’t compelled to take a free item if one were offered to them? Social engineers know this and will often use tactics such as providing free advice, exclusive or personalized, to make the victim feel as if they owe the attacker something in return.
Commitment – Most of us feel a strong need to follow through with something if we promise to do it. Social Engineers know this and urge the victim to agree to small things before going for the primary goal. They also may get them to agree to do something before the victim realizes the risk.
Social Proof – People are more willing to buy into something if they think their friends have. With research, the hacker can quickly gain information on who our friends our to name drop and make us feel like they are a trusted source since they also know our “friend.”
Authority – Who would you be more likely to believe about a supposed health product to solve all your problems? A doctor or some random email claiming to know it all? Should that email come from a “Dr.” you will probably give it more authority than another unexpected voice. Hackers exploit this by claiming “according to experts” or “science proves” to gain your trust and convince you to agree to something.
8 Techniques of Social Engineering Attackers
While there may be more techniques, these are the most common ones you are likely to come across if a social engineering attacker targets you. They are:
- Baiting – uses our sense of curiosity, or even greed, to draw you in. This usually results in you installing, or clicking on, something that will download malware onto your system.
- Water Holing – casts a broader net. The attacker will target a group of specific individuals by infecting sites they regularly visit and trust, knowing they feel safe on those pages.
- Scareware – If we feel under attack, our fight or flight response is triggered. Taxes are overdue, foreclosure notices or the threat of disconnected utilities have been known to trigger an immediate response to protect yourself. Scareware uses this to get you to react to protect yourself, and no surprise, but they have the solution to take care of it then and there.
- Quid Pro Quo – attacks generally involve the attacker offering something to the victim in exchange for a password or specific action. Such as a caller claiming to be from IT who then asks you to download a particular program to your computer, which is most likely to be malware.
- Pretexting – is where an attacker pretends to be someone they aren’t (your boss, grandchild, long lost cousin) and tricks you into giving them sensitive information.
- Honey Trap – With online dating opening up more expansive pools of potential romantic partners, cyberattackers have also tapped into this area to take advantage of human emotions. A honey trap is where the attacker poses as a love interest, then tries to gain information or money due to their growing relationship.
- Tailgating – We’ve all seen it happen. You enter a secure building with your credentials, and someone pops up right behind you. General courtesy says to hold the door open, which is exactly what the attacker is looking for.
- Phishing, Spear Phishing, and Vishing – Like baiting, the attacker uses your sense of urgency or natural curiosity to encourage you to click a link or give out private information. Spear phishing attacks gather a bit more information on you before launching their attack, and vishing uses the same strategies as phishing and spear phishing but is over the phone and using voice communications.
Basic Security Habits to Keep You Safe
There are many tools and processes that you can use to keep yourself and your business safe, but below are the big 4.
- Don’t click! Just don’t do it. If you receive an email or text from an unknown source telling you to click here now, your account is in jeopardy, or whatever you do, don’t click that link. If you are concerned, navigate directly to the account through your typical methods of accessing, such as a web browser or a mobile app.
- Password managers. Just use them. Google and Apple have robust password management systems you can tap into that can follow you from device to device.
- Multi-factor authentication. As annoying as they are, two factor authentication processes are critical in keeping you safe online. Any attempt to log into your account requires you to respond to a text or phone call or email you can be warned immediately of a potential breach and act accordingly.
- Be careful of online friends. Yes, the internet and social media can be significant in helping you to form new relationships or maintain old ones. But take a good look at friends who refuse to talk on the phone or meet in person – they may not be real.
The Greatest Defense is Education
You know the old NBC slogan “The More You Know?” The more you know about the tactics and tricks, the more you will be able to recognize them before falling victim. And if you think you were a victim, call in a cyber security expert immediately to secure your systems and information and also help you keep further attacks from affecting you.
Letter from the President/CEO
98%. That number continues to astound me. That the majority of attacks that are attempted are done so with the tactics of social engineering. Even the most tech savvy can inadvertently fall victim to these techniques as they are so well built on human psychology and behavior. But also, as said above, the more you know the less of a risk there is. Have you educated your business of the dangers of social engineering and how to recognize a potential attack? Do you have a process in place should an employee report one or (hopefully not) falls victim?
Did you know we offer a free security audits? We’d love to do a health check on your security protocols, especially in the area of social engineering, and make sure you are as protected as you can be. Give our office a call at 502-266-7700 and schedule yours today. It won’t cost you anything to check…but it could cost you a bundle if you don’t.
Hope to talk to you soon!
Dan Kanabroski
Director of Sales and Marketing
dkanabroski@warrentechnology.com
WarrenTechnology.com
502/266-7700